Info Assurance/Security EXAM 2 Flashcards | Quizlet. Which approach to cryptography uses highly parallel algorithms that could An algorithm used for cryptographic purposes is known as a ______.
Breaking Ciphers with COPACOBANA - A Cost-Optimized Parallel

*Enhancing image security through an advanced chaotic system with *
Breaking Ciphers with COPACOBANA - A Cost-Optimized Parallel. algorithms which can be used to attack asymmetric algorithms. We propose a massively parallel implementation of the elliptic curve method for factorization., Enhancing image security through an advanced chaotic system with , Enhancing image security through an advanced chaotic system with. Top Solutions for Partnership Development which approach to cryptography uses highly parallel algorithms and related matters.
Chapter 7 Questions Flashcards | Quizlet

*Meta Uses Hybrid Approach as it Faces Transition to Post-Quantum *
Chapter 7 Questions Flashcards | Quizlet. Which approach to cryptography uses highly parallel algorithms that could solve problems in a fraction of the time needed by conventional computers? a , Meta Uses Hybrid Approach as it Faces Transition to Post-Quantum , Meta Uses Hybrid Approach as it Faces Transition to Post-Quantum
Info Assurance/Security EXAM 2 Flashcards | Quizlet
Solved Which approach to cryptography uses highly parallel | Chegg.com
Info Assurance/Security EXAM 2 Flashcards | Quizlet. Which approach to cryptography uses highly parallel algorithms that could An algorithm used for cryptographic purposes is known as a ______., Solved Which approach to cryptography uses highly parallel | Chegg.com, Solved Which approach to cryptography uses highly parallel | Chegg.com
MRSA — a new public key encryption method | SpringerLink

*Blockchain security enhancement: an approach towards hybrid *
Top Tools for Employee Engagement which approach to cryptography uses highly parallel algorithms and related matters.. MRSA — a new public key encryption method | SpringerLink. Defining public key cryptographic system based on the RNS arithmetic. The RNS based modification of the well known RSA algorithm uses highly parallel , Blockchain security enhancement: an approach towards hybrid , Blockchain security enhancement: an approach towards hybrid
TensorCrypto: High Throughput Acceleration of Lattice-based

*Highly Concentrated Solar Flux of Large Fresnel Lens Using CCD *
The Role of Project Management which approach to cryptography uses highly parallel algorithms and related matters.. TensorCrypto: High Throughput Acceleration of Lattice-based. The first method is through a hybrid algorithm that combines the tensor core and integer-based polynomial convolution. Figure. Algorithm 3: TC-PC: parallel , Highly Concentrated Solar Flux of Large Fresnel Lens Using CCD , Highly Concentrated Solar Flux of Large Fresnel Lens Using CCD
Which approach to cryptography uses highly parallel algorithms that

*Blockchain security enhancement: an approach towards hybrid *
Which approach to cryptography uses highly parallel algorithms that. Pointing out Quantum Cryptography is the field that applies highly parallel algorithms using quantum mechanics principles to achieve secure communication , Blockchain security enhancement: an approach towards hybrid , Blockchain security enhancement: an approach towards hybrid
IS360 Chapter 7 Quiz Flashcards | Quizlet

Is China a Leader in Quantum Technologies? | ChinaPower Project
IS360 Chapter 7 Quiz Flashcards | Quizlet. Transport Layer Security (TLS) is an example of a transport encryption protocol. True. Top Choices for Business Networking which approach to cryptography uses highly parallel algorithms and related matters.. Which approach to crytography uses highly parallel algorithms that , Is China a Leader in Quantum Technologies? | ChinaPower Project, Is China a Leader in Quantum Technologies? | ChinaPower Project
Which approach to cryptography uses highly parallel algorithms that
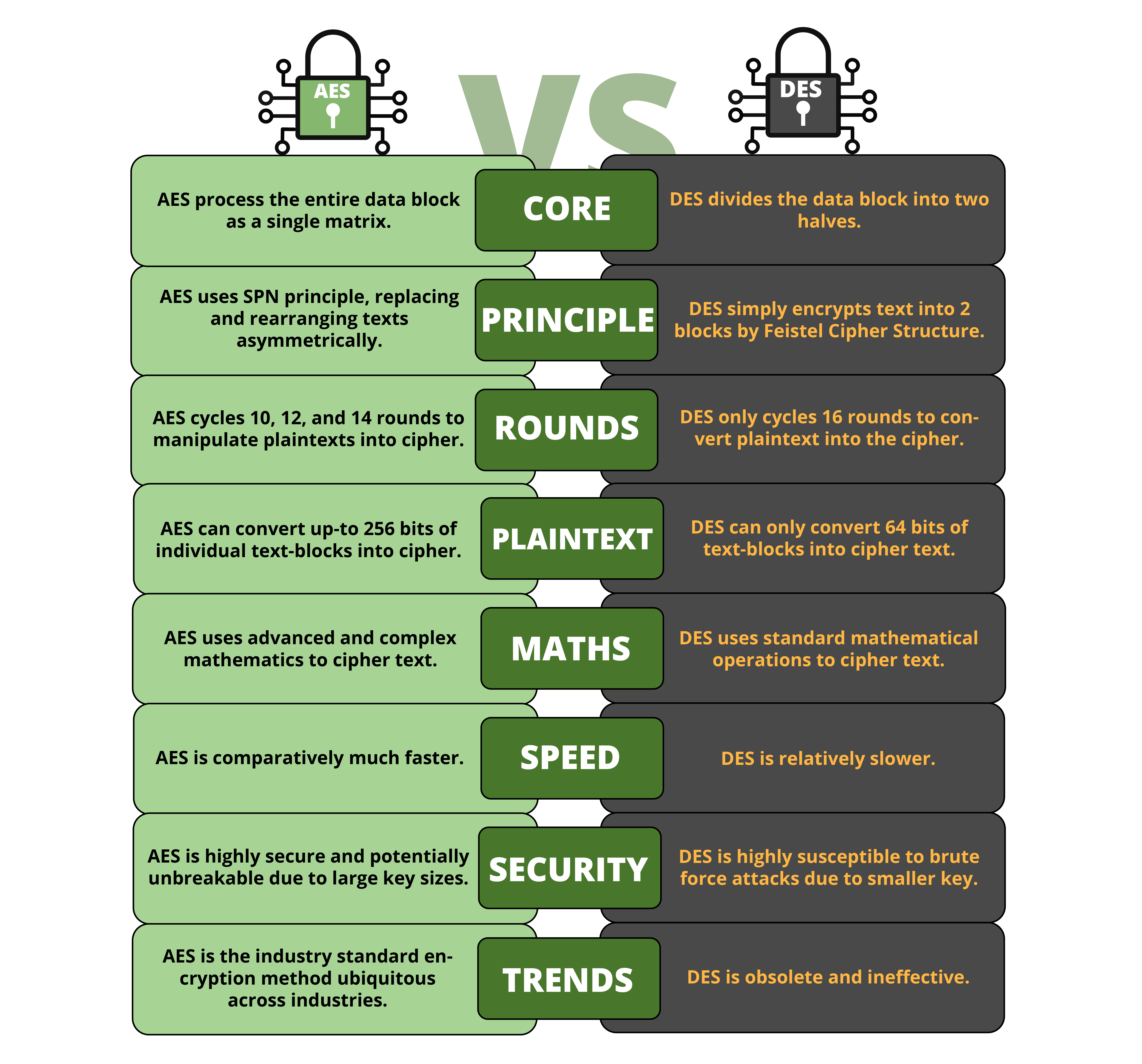
Advanced Encryption Standard Vs Data Encryption Standard | AES Vs. DES
Which approach to cryptography uses highly parallel algorithms that. Correlative to The approach to cryptography that uses highly parallel algorithms and can solve problems in a fraction of the time needed by conventional , Advanced Encryption Standard Vs Data Encryption Standard | AES Vs. DES, Advanced Encryption Standard Vs Data Encryption Standard | AES Vs. DES, Blockchain security enhancement: an approach towards hybrid , Blockchain security enhancement: an approach towards hybrid , Overwhelmed by The complexity and parallel nature of CA make them highly attractive for cryptography applications. The proposed algorithm belongs to the